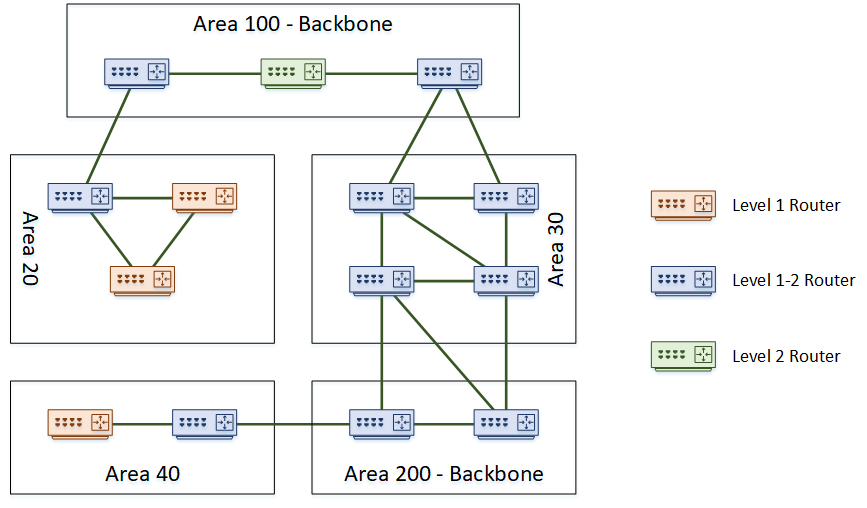
As the history of IS-IS is in the OSI stack, some of the components are a bit different to what we’re used to in the TCP/IP world. Let’s clear up a few of the terms.
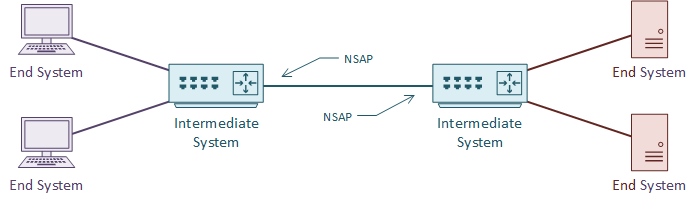
An IS is an Intermediate System. This is the ISO name for a router, and how IS-IS gets its name. It is communication between intermediate systems, or routers.
An ES is an End System. This is a device on the network, such as a server or workstation. In the original specification, an ES would take part in IS-IS. It would have no need for DHCP or FHRP, as it would already have a local routing table.
CLNS (Connection-Less Network Service) is a network service in the OSI stack. CLNP (Connection-Less Network Protocol) is the protocol that implements CLNS. If you’re more familiar with TCP/IP, this feels unusual. TCP/IP does not separate the service and the protocol in this way. This will make more sense with time.
An NSAP is a Network Service Access Point. This is a layer-3 address, for CLNS packets. This is like an IP address in the TCP/IP stack. IS-IS uses NSAP addresses for communication, not IP addresses. Again, this will make more sense as we go through the article.
TLV
TLV, or Type Length Value are the payload fields in IS-IS. The TLV fields carry routing information. IS-IS does not care what goes in these fields, which makes it protocol agnostic. This is a bit like shipping containers; The ship doesn’t care what’s in the containers.
IS-IS uses CLNS for transport. Each router has an NSAP address for sending and receiving link state information. The link state information may contain several TLV fields.
It is common to put IP routing information into the TLV’s. But any sort of data can be in there. It’s up to the receiving router to know what to do with the information.
Metric
Like OSPF, IS-IS uses cost as a metric. The specification says that this can be either a wide or narrow value. Cisco routers only support the wide metric. The narrow metric is not suitable for MPLS Traffic Engineering. The wide metric uses 24 bits for the link metric, and 32 bits for the path metric.
All links have a cost of 10 by default. This means that in a default implementation, hop-count forms the metric. It is up to the network designer to select a more suitable cost scheme.